The basic principle of RFID (Radio Frequency Identification) is to install an electronic tag on a recognized object. When the identified object enters the reading range of the RFID system, the radio frequency identification technology uses radio waves or microwave energy to conduct non-contact two-way communication. Implement identification and data exchange capabilities.
The tag sends the carrier information to the reader. The reader receives the information and decodes the data. The data collected by the reader is sent to the back end for processing through the serial port, and is transmitted to the server through the network. This completes the collection and processing of the information. The process to achieve the purpose of automatically identifying the identified objects.
The architecture of the RFID application system is shown in Figure 1. It is basically composed of a reader, an antenna, and a tag, as well as a background enterprise application system. Non-contact coupling of radio frequency signals between the tag and reader/writer through coupling elements. There is a middleware in the system responsible for completing the system and a variety of readers to adapt the data obtained from the tag reader to filter, in order to reduce network traffic. The tag communicates with the reader through the air interface protocol. The communication between the reader and the middleware is defined through the reader/writer protocol. The communication interface between the middleware and the application system is specified by the ALE protocol.
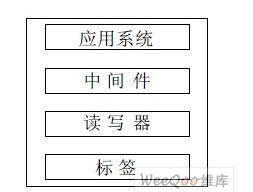
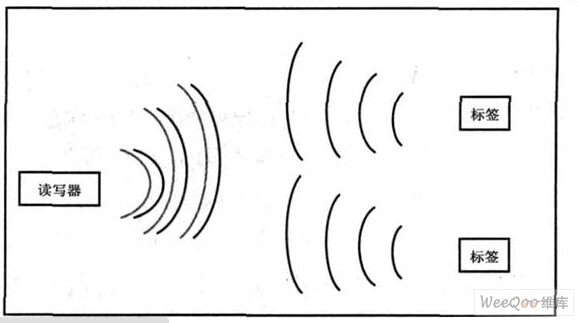
Figure 2 shows the communication process between RFID system readers and tags. The readers and tags exchange data through RF electromagnetic fields.
The reader first sends a continuous carrier signal, and sends various read/write commands through ASK modulation, etc. The tag responds to commands issued by the reader through backscatter modulation and returns information such as EPC (Electronic Product Code).
2. Air Interface Protocol As shown in Figure 1, the protocols involved in the RFID system have their own specifications from the bottom layer to the top layer. According to the different power modes of the labels, the RFID system can be divided into active systems and There are two kinds of passive systems; according to the different frequency bands of system work, RFID systems can be divided into low-frequency, high-frequency, ultra-high frequency and microwave frequency bands. The paper mainly discusses the key technologies of the ultra-high frequency passive RFID air interface protocol.
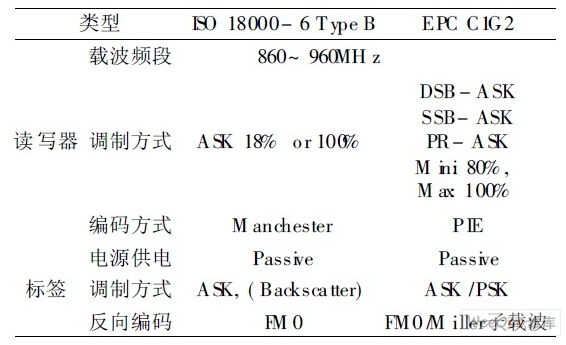
The current UHF RFID air interface protocols are mainly ISO18000-6TYPEB protocol and EPC Global Class 1 GEN2 protocol (EPCC1 GEN2 protocol, which has now become ISO 18000-6 TYPEC). The two protocol pairs are shown in Table 1. In general, the definition of the EPCC1GEN2 air interface protocol is more complete, and most existing products follow such protocols. In addition, ISO18000-6 basically conforms to the specifications of some existing RFID vendors' product specifications and the EAN-UCC proposed label architecture requirements. It only specifies the air interface protocol, which has no restrictions on data content and data structure and can therefore be used in EPC. Therefore, the EPC protocol has been widely used as a de facto standard.
The air interface protocol includes the physical layer and media access control (MAC) layer. The physical layer includes the frame structure definition of data, modulation/demodulation, encoding/decoding, link timing, etc. The MAC layer contains the link timing, interaction process, and defense. Collision algorithm and security encryption algorithm.
2.1 Physical layer EPC protocol, forward communication using double sideband amplitude shift keying (DSB-ASK), single sideband amplitude shift keying (SSB-ASK) or reverse phase shift keying (PR-ASK) and other modulation methods . The tag uses the reader's RF electromagnetic field to obtain operating power energy. The reader obtains the information of the tag by sending an unmodulated RF carrier and listening for the backscattered reply of the tag. The tag transmits information by backscatter modulating the amplitude or phase of the RF carrier. The encoding format is selected by the tag according to the reader command and can be FM0 or Miller modulated subcarriers.
In terms of link timing, the EPC protocol stipulates that the reader sends different commands, and the time interval between the reader sending the command and the tag response command is the largest, the smallest, and the typical time.
In terms of data frame structure, the EPC protocol specifies the reverse data rate, encoding method, etc. by specifying the preamble before the command is queried. Before the other commands use the frame synchronization code to achieve synchronization. The reverse frame synchronization code has poor autocorrelation performance, and the reverse frame synchronization code can be modified to further improve its autocorrelation.
In the EPC protocol, forward communication adopts PIE encoding of different lengths, which simplifies the decoding algorithm at the tag end. In addition, the PIE code also carries clock information. In the communication process, data synchronization can be well maintained and various wireless interferences can be resisted, thereby improving the reliability of the system in a wireless environment. Reverse communication uses FM0 or Miller subcarrier coding.
For signal modulation, the reader communicates with the tag using DSB-ASK, SSB-ASK, or PR-ASK modulation. The tag should be able to demodulate all three modulation types.
ASK modulation is modulated by digital data and takes different values. It is demodulated by envelope detection, which is suitable for the characteristics of electronic tags. PSK adjusts the carrier phase with data values ​​that need to be transmitted. This modulation technique has better anti-interference performance. Phase changes can be used as timing information to synchronize the transmitter and receiver clocks.
2.2 MAC Layer 2.2.1 Tag Access Control The reader manages the tag population by selecting, inventorying, and accessing three basic operations. The reader selects the tag population to inventory and access the tags. This operation is similar to selecting records from the database. The reader initiates a round of inventory by issuing a query command in one of the four sessions. There may be one or more tag responses. If a single tag responds, the reader requests the tag's PC, EPC and CRC-16. If multiple tags respond, the anti-collision process is entered. The tag must be uniquely identified before the reader and individual tags are read or written. Each operation accessed includes multiple commands.
2.2.2 Anti-collision algorithm In the process of tag access control, the reader responds to multiple tags in one round and requires the reader to perform collision arbitration. The ALOHA algorithm is used in the EPC protocol, and the Binary Tree algorithm is used in the ISO18000 protocol to solve the anti-collision problem. However, the efficiency of the ALOHA algorithm is only 33%. The number of labels needs to be solved. The Bianry Tree algorithm is lower, and the problem of fast label dispersion needs to be solved. Therefore, the paper proposes to use multi-tree algorithm to quickly distribute labels and improve the anti-collision efficiency.
2.2.3 Secure Encryption During a read operation, the reader issues a read command to the tag, which then transmits the clear data according to the read command. During a write operation, the reader requests a random number from the tag. The tag transmits the random number to the reader in clear text. The reader uses this random number to perform an exclusive-OR operation with the data to be written. The tag, the tag will get the data after XOR again get clear text and write to memory. When the access instruction and the kill instruction are executed, the reader first requests a random number from the tag before sending the password, and sends a password that has been XORed to this random number to the tag to achieve the data from the reader to the tag. The purpose of being covered on the forward channel.
In the EPC protocol, passwords are transmitted without protection in the air, and any reader can read and write data to the chip. Although the EPC protocol specifies the use of an access code to protect the data in the chip, this access code is directly transmitted unprotected over the air between the chip and the reader. This makes the password insecure, providing the possibility for password cracking and cannot guarantee data security.
3ã€Conclusion
In the RFID application, it is necessary to solve the interface standard problem of each layer, and the air interface protocol is the basis. The air interface protocol needs to solve the issues such as link timing, frame structure, encoding mode, and modulation mode of the physical layer. MAC focuses on solving access control protocols, collision avoidance algorithms, and security encryption algorithms.
brass valves can handle the toughest jobs, under the worst conditions. Brass valves are known for various qualitative features such as adaptability and flawless performance.
JKLONG brass valves are produced in modern factories used exclusively for valve manufacturing. Each phase of the manufacturing process, from selection of raw materials to casting, forging, machining, assembly and testing, has been improved with automated production facilities and unparalleled production technology. Standardization and automation yield JKLONG brass valves of superior quality and higher uniformity at competitive prices supported by incomparably prompt delivery.
Brass Valve,Forged Brass Valve,Brass Angle Valve,Brass Gate Valve
Ningbo Jiekelong Precision Manufacturing Co., Ltd. , http://www.jklvalve.com
